Share
In today’s connected world, over-the-air (OTA) updates have become a built-in necessity for modern embedded systems. It’s how teams deliver fixes and features without waiting for the next manufacturing cycle or a technician on-site. It’s no secret that IoT is moving fast. McKinsey projects that IoT could create up to $12.6 trillion in economic value by 2030, with most of this value coming from B2B devices that rely on secure, resilient firmware to keep operations running smoothly. If you’re building for that future, your OTA update strategy has to be just as bulletproof as your firmware.
But if you’ve ever shipped firmware at scale, you know it’s not just about pushing new bits. The real work is in ensuring the update applies across silicon variants, your devices won’t run out of flash halfway through, and that there’s a safe way to roll back if something goes sideways.
In this blog, we’ve created a battle-tested OTA update checklist developed by firmware engineers who have shipped updates at scale. It’s grounded in real-world deployments, proven in the field, and shaped by the lessons our team has learned firsthand.
TL;DR
A brief look at what the checklist holds:
- Foundational steps to architect a secure, scalable OTA system from day one
- A checklist to validate hardware and firmware compatibility before you even think about shipping
- How to build rollback logic that works in the wild
- Security safeguards that go beyond “just use TLS”
- Fleet rollout techniques that minimize blast radius
- And post-deploy signals to catch failures early, before customers do
Before we jump to the OTA update checklist, let’s learn why OTA updates usually break and what necessary steps can be taken to prevent it from happening.
And, if you’re looking to go deeper on how to simulate failures and build resilient OTA tests, check out our OTA Testing 101 guide.
Why OTA Updates Break and How to Prevent It
Most failed OTA updates don’t crash because of one big problem. They fail because of a dozen small ones that slip through the cracks. It could be a power loss mid-flash, an expired certificate, or a firmware mismatch that slipped through because the test matrix missed an edge case.
If you’ve seen devices get stuck in a boot loop after a bad update, you know how fast a minor issue can escalate. Sometimes it’s a checksum mismatch that bypasses rollback. Other times, the bootloader accepts a payload that was never validated against the production hardware.
To prevent this from happening, you need to know which devices are safe to update and which ones aren’t. Your rollback path should not only exist but also be tested in production-like conditions. And you need to be able to make data-driven decisions about how the rollout is proceeding, with systems that flag failures before your users do.
To learn what a robust OTA process entails, read on.
How to Architect A Robust OTA System (Build-Time)
We’ll start with the foundational steps around infrastructure. If you’re working specifically with embedded Linux devices, you’ll also find this detailed OTA guide helpful for navigating Linux-specific validation and deployment strategies.
Step 1: Set Up OTA Infrastructure and Device Inventory
Before you even consider pushing an update, ensure your OTA backend is wired into your CI and release pipeline. Every device in the fleet should be tagged with meaningful metadata like firmware version, SoC revision, modem firmware, and battery chemistry. These factors can all influence how a device responds to an update.
You want to be able to filter your fleet fast. If a batch of devices requires a full image instead of a delta, you should be aware of this before rollout begins. Your OTA backend should support both delta and full-image paths and apply logic to switch based on available bandwidth, memory, or firmware version jump.
Step 2: Enable Logging, Crash Reporting, and Rollback
Once the update rolls out, you need a way to quickly identify if anything has broken. Logging should cover install events, reboots, and error paths. Crash reporting should remain active throughout the update window, not just after, so you can catch issues as they arise.
Rollback should be your working safety net when anything goes south. With failure-handling in place, you’re ready to validate compatibility across every firmware and hardware variant in your fleet.
Step 3: Ensure OTA Firmware and Hardware Compatibility
Check that the update installs cleanly across all supported firmware versions and hardware SKUs. Devices on older firmware may need an intermediate version to migrate cleanly. Your bootloader should reject firmware images that don’t match the device’s expected hardware configuration or firmware lineage, and should flag version conflicts early to prevent accidental bricking.
If your fleet spans different chip revisions or peripherals, confirm builds are tagged and gated correctly. Don’t assume compatibility just because it passed on your dev kit. Once you’re confident the update can run on anything you ship, the next step is to secure the image and the channel it moves through.
Step 4: Implement Secure OTA Updates with Signing & Hashes
Protect your OTA update at rest and in transit, and sign the final image using a proven scheme like RSA or ECDSA. Embed a hash check that runs before the install starts. If the signature or checksum fails, the device should never apply the update.
Keep your signing keys safe and rotate them if needed. For fleets using OTA monitoring tool software, signature enforcement can be built into the delivery pipeline.
With the update locked and verified, ensure that the network path remains secure. Certificates come next.
Step 5: Check TLS Setup and Certificate Expiration
TLS missteps frequently cause OTA updates to silently fail. Make sure your root certificates and any intermediate certs are still valid. Devices stuck with expiring certs won’t even connect to download updates. For long-lived fleets, consider automating cert rotation using protocols like EST or ACME to reduce manual overhead.
Once certs are in place and trust is verified, you can lock the build and prepare it for release.
Step 6: Lock the Final Build and Save Debug Artifacts
After cert validation, freeze the build. Tag the exact commit and confirm it’s reproducible. Track ELF builds using semantic versioning or Git tag hashes so your debug artifacts match binaries one-to-one across environments.
Save every debug artifact you may need later, including map files, symbol tables, stripped, and unstripped binaries. If a crash surfaces in production, having the matching .elf and debug symbols is the only way to get a full backtrace.
If you happen to be using an open-source solution like Hawkbit, which has since been deprecated, learn how to move forward without putting your fleet at risk.
Before You Hit Send: OTA Update Rollout Checklist (Deploy-Time)
Devices might leave the factory identical, but the moment they power on in the real world, conditions diverge. Variations in usage patterns, battery age, thermal cycles, and connectivity begin to influence their behavior. Even when hardware and firmware match, assumptions based on uniformity break quickly in production.
Rolling out firmware as if every device is in the same shape or environment is where many updates go wrong. Our checklist comes from lessons we’ve learned the hard way or seen teams trip over when one device in a thousand fails silently.
Run through this checklist before shipping updates to your fleet, especially at scale.
✓ Define Which Devices Should Get the Update
Not every device should update at once. Establish rules based on hardware version, firmware lineage, and other relevant metrics. Exclude items with known connectivity issues or low storage capacity. Tag devices by cohort so you can split them into canary, staging, and full deployment phases.
If a device hasn’t been reported in days, hold off. If it’s still on a legacy bootloader, validate that path first. Avoid assumptions and gate by data. With the targeting set, now we test the OTA itself.
✓ Test OTA Internally for Firmware Stability
During internal OTA testing before launch, use controlled brownouts, dropped packets, or reboots mid-flash to identify any issues that may arise. Confirm your bootloader recovers cleanly, and the rollback logic kicks in when needed. Validate all success signals by checking:
- The device rebooted cleanly
- The device is rebooted cleanly, reported a firmware version (new or rollback), and remains in a known-good, operational state.
- Logs were uploaded successfully
Edge failures usually show up here, not later. Testing like this helps you catch silent failures before your users do. For more controlled validation, consider using test harnesses or a HIL (Hardware-in-the-Loop) setup to simulate edge conditions, such as packet loss or reboots mid-write.
Want to go deeper into building robust test scenarios? Read our OTA Testing 101 guide.
✓ Beta OTA Rollout Testing in Real-World Conditions
Push the update to a small controlled group of test devices in real environments. These should mirror production hardware, connectivity, and edge cases. Watch your telemetry closely. Are failure rates creeping up? Did watchdogs trip? Are logs reporting as expected?
This is where unexpected issues like LTE dropouts or low memory conditions surface. Use this phase to validate install stability and real-world behavior under variable conditions.
If this round holds, you’re ready to start checking if the devices themselves are ready for the update.
✓ Check Device Health Before Sending OTA
Before you trigger the update, ensure the device is healthy enough to receive it. That means:
- The battery must be above a safe threshold.
- There’s enough free flash to download and unpack the update
- RAM and stack usage aren’t already under pressure
If any of these are red flags, hold the update. You can automate these checks with fleet health reports and filters inside your OTA pipeline. Devices that don’t meet the bar can be retried later.
Once you’ve cleared the basics, the next move is to prep your safety nets.
✓ Final Go or No-Go with Engineering and Support
This is the handoff moment. Before the update goes into production, verify that alerting, device monitoring, and rollback triggers are active. Ensure that support teams are aware of what’s being sent out and how to identify failures early. If you’re using any monitoring tool, confirm that dashboards are filtering the right cohorts and signals.
No one wants to be surprised by a spike in crash-free sessions. Once the team is confident, the lights are green across tooling and people, you’re cleared for a controlled launch.
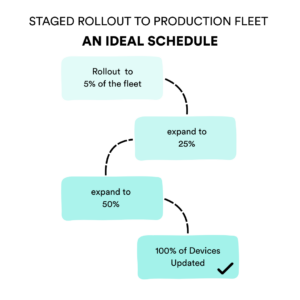
✓ Conduct Staged OTA Rollout Strategy with Live Monitoring
Always start small and roll out the OTA update to 5% of the fleet. Set hard thresholds for failures and don’t auto-expand if you see error rates climb. Use OTA tooling that supports gating and cohort control.
An OTA monitoring software can flag crash spikes, boot loop increases, or memory regressions before they scale. Once you confirm stability, step up in phases. This keeps your release safe and your team out of firefighting mode. From here, post-deployment monitoring takes over.
For reference, this documentation outlines the process for tracking release builds, version artifacts, and delivery metadata in production OTA systems.
OTA Testing in Review: What Separates Good from Great
Once the update hits production, your job shifts from building to monitoring. Devices may look healthy on paper, but patterns only emerge over time. You’ll want to keep an eye on any crash data reported by devices, install success metrics, and watchdog activity across cohorts. Did the firmware boot as expected? Are logs still uploading? Is memory holding stable under normal operation?
OTA monitoring tools help you answer those questions with confidence. They give you visibility into how updates behave in the field, not just how they looked in your test lab. That’s your signal to ramp safely or catch the edge cases before users do.
Ready to Ship OTA Updates with Confidence?
Memfault gives embedded teams everything they need to ship OTA updates without second-guessing. From cohort-based rollouts and incremental staged rollouts to crash analytics and fleet-wide monitoring, it’s the end-to-end platform for managing firmware in production.
A screenshot of OTA release dashboard in Memfault.
If you’ve made it this far, you’re probably ready to start shipping updates that work the first time. But doing it at scale means solving more than just firmware delivery. You need safe rollouts, crash visibility, and a way to test every device path before it ships.
We put together a session on how teams are building secure, resilient OTA pipelines that don’t fall apart under pressure.
Catch the full session here → Webinar: The Secrets to Building Secure and Scalable OTA Infrastructure
OTA Update Checklist FAQs
How do I create a reliable OTA update checklist?
A reliable OTA update checklist begins with clear visibility into your device inventory, firmware lineage, and the current health status of each device. From there, implement secure image signing, active rollback logic, and OTA tests that simulate edge conditions, such as power loss or packet drop. Once deployed, monitor crash reports, update success rates, and device vitals in real time.
What should I include in an OTA firmware update process?
An effective OTA process should include device targeting rules, battery and power state validation, bootloader compatibility checks, cryptographic signing, TLS setup, and telemetry instrumentation. These components are foundational to delivering updates safely and should be treated as essential, not optional.
Why do most OTA updates fail?
OTA updates commonly fail due to power loss during transmission, expired TLS certificates, and firmware version mismatches. In many cases, the root cause is an untested rollback path or an edge case that the test matrix missed. Building resilience into each layer of your update flow prevents these issues from escalating in production.
How can I prevent device bricking during OTA?
To prevent devices from bricking, maintain a local fallback image, enforce CRC checks or watchdog timers, and test rollback logic under failure scenarios. Your system should treat failure as a standard path and recover gracefully. A strong crash monitoring system will also help surface silent issues early.
How often should I test my OTA system?
Your OTA system should be tested with every firmware release. This includes simulating network instability, incomplete downloads, and power interruptions. OTA testing is a continuous part of your CI process, ensuring real-world reliability.
What tools help with managing OTA for embedded devices?
Tools like Memfault help embedded teams manage OTA updates with full-stack observability, rollback support, and staged rollout controls. With Memfault, you can track delivery success, monitor fleet health, and debug failures across all deployment phases from one platform.
Citations
- IoT value set to accelerate through 2030: Where and how to capture it, By Michael Chui, Mark Collins, and Mark Patel, McKinsey & Company
- “How to Test OTA Updates without Bricking Devices ”, Siara Singleton, Memfault.
- “OTA for Embedded Linux Devices: A practical introduction”, Thomas Sarlandie, Memfault
- “How To Test Your IoT Product Before Launch”, Jesse Dukes, Memfault
- “hawkBit Has Sunsetted their OTA System’s UI: What’s Next for Embedded Teams”, Pat Wolfe, Memfault
- “OTA IoT Breakdown: What OTA Is and How It Works in IoT”, Siara Singleton, Memfault.
- “Over-the-Air Updates (OTA) | Memfault Docs” Memfault Docs.
- “Manage OTA updates for millions of devices”, Memfault Product Page
- Webinar: The Secrets to Building Secure and Scalable OTA Infrastructure