Share
Updating IoT devices manually isn’t just inconvenient, it’s a liability. Without a scalable Over-the-air (OTA) update process, companies risk increased operational costs, security vulnerabilities, and outdated firmware that exposes devices. As IoT adoption accelerates, relying on manual interventions for software maintenance becomes unsustainable.
The number of connected IoT devices is projected to exceed 29 billion by 2030, reinforcing the need for seamless device management at scale. OTA updates have emerged as a critical solution, enabling developers to push firmware updates, security patches, and performance improvements remotely without disrupting end users or requiring manual intervention.
We’ll explain what OTA updates are, how they work, and why they’re essential in 2025 and beyond. We’ll cover:
- The core technology behind OTA updates
- Why OTA updates are essential for modern IoT fleets
- Key stages for a successful OTA rollout plan
- Why are OTA updates a wise investment
To understand why OTA is essential, let’s break down what it is, how it works, and why it’s become the standard for managing connected devices.
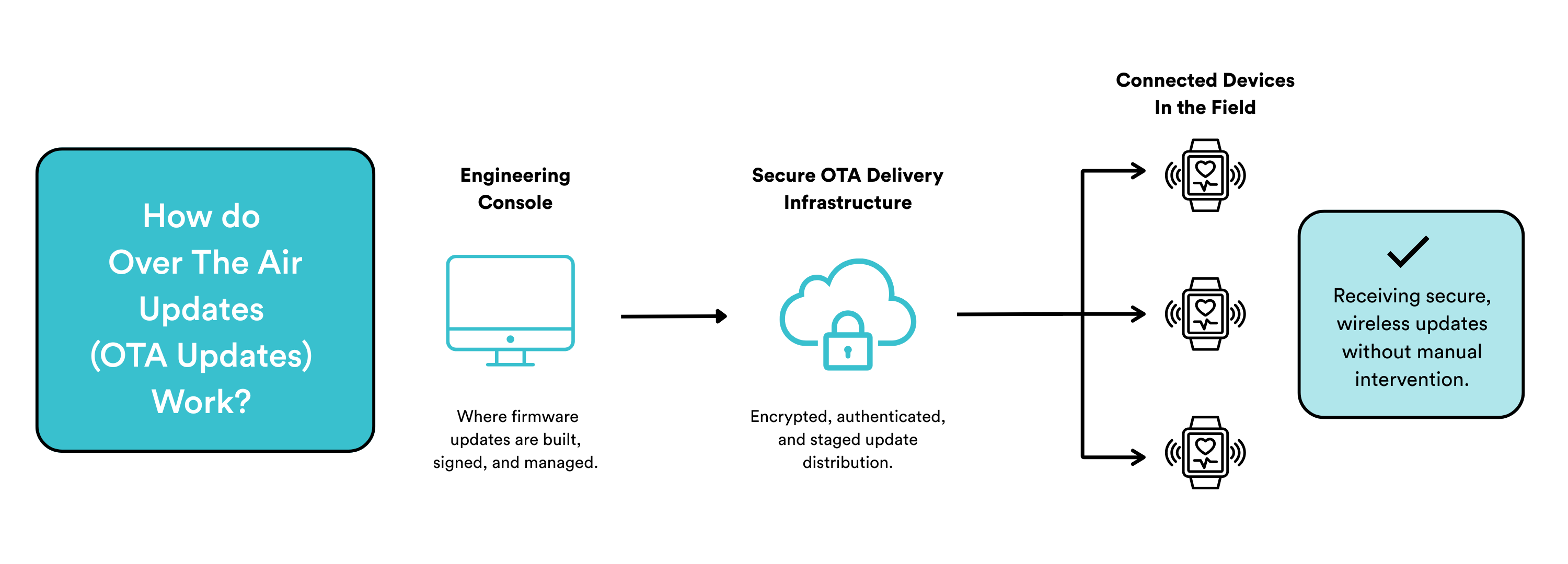
What is OTA in IoT?
Over-the-Air (OTA) updates allow IoT devices to receive firmware and software updates remotely via the cloud, eliminating the need for manual access. Engineers can deploy updates wirelessly over Wi-Fi, cellular networks, or Bluetooth, ensuring devices remain secure, functional, and up to date at scale. OTA technology helps reduce maintenance costs, enhance security, and improve device performance without manual intervention.
How does OTA work?
OTA updates deliver new firmware or software to cloud-connected devices. They can be deployed automatically, staged for gradual rollout, or manually triggered by engineers. Before installation, devices authenticate and verify updates to ensure security, preventing unauthorized modifications or corrupted firmware from disrupting operations. This process ensures that devices remain functional and secure throughout their lifecycle.
The Evolution of OTA Updates
Before Over-the-Air (OTA) updates, engineers had to manually connect to each device to update firmware, a slow and costly process that made large-scale deployments difficult. Early OTA implementations introduced remote updates but lacked security measures, rollback mechanisms, and targeted deployment options.
Today, OTA technology is more advanced, with stronger encryption, authentication protocols, and safeguards against unauthorized updates. Rollback capabilities ensure that devices can revert to a stable version if needed. Staged rollouts and device cohorts allow engineers to test updates on smaller groups before full deployment, reducing risk and improving control.
Believe it or not, some engineering teams still operate without a solid OTA infrastructure. They’re struggling with workflows like:
- Manual firmware updates that require direct physical access to devices make large-scale deployments inefficient.
- Limited visibility into update success rates, leading to unknown failure points and troubleshooting delays.
- Inconsistent rollback mechanisms leave devices vulnerable to faulty updates without a way to revert.
- Security gaps in update delivery increase the risk of unauthorized firmware modifications.
- Lack of staged deployments forces teams to roll out updates to the entire fleet at once, raising the stakes if issues arise.
This lack of robust OTA infrastructure not only slows down development but also introduces unnecessary risks and inefficiencies.
Why OTA Updates Matter for IoT Devices
IoT devices are becoming more complex, with hardware and software working together in ways that demand continuous updates. In fact, the software layer is now a growing share of the product’s value. From feature rollouts to performance tuning, OTA updates are how manufacturers continuously improve devices after they ship.
One real-world example: A connected coffee maker was named “Best Automated Pourover” after a firmware update added simple brew presets that made it easier to use. Users immediately noticed the improvement and praised how intuitive the software had become.
It’s also important to remember that consumer devices don’t operate in a controlled environment. They connect to phones, home networks, and third-party peripherals that change constantly. It’s impossible to predict every compatibility issue at launch. Maintaining security, efficiency and reliability on top of basic functionality all requires a structured approach to software management. OTA updates give teams a way to respond quickly, fix bugs in the field, and adapt to changes across the broader ecosystem.
Security and Compliance
OTA updates play a critical role in mitigating vulnerabilities by enabling remote patching of security flaws in real time. Without them, IoT companies risk exposing devices to cyber threats, making rapid deployment of security fixes a necessity rather than a convenience. Regulatory requirements also shape the need for OTA capabilities. The Cyber Resilience Act in the EU and the U.S. Cyber Trust Mark set higher security standards for connected devices, requiring manufacturers to ensure software remains up-to-date. In regulated industries, OTA updates are no longer optional—they are essential for compliance and long-term device security.
Cost and Efficiency
Reducing operational costs is a significant advantage of OTA updates. By eliminating the need for manual firmware updates, companies can cut expenses related to on-site servicing, customer support, and device logistics. OTA also helps prevent unnecessary return merchandise authorizations (RMAs), where devices are sent back due to software issues that could have been resolved remotely. Keeping devices in the field longer without costly recalls or replacements significantly improves overall efficiency.
Reliability and Product Improvement
OTA updates allow companies to extend the usefulness of IoT devices by continuously adding new features, optimizing performance, and fixing issues before they impact users. Instead of relying on customers to report problems, teams can proactively monitor device health and push fixes as needed. This approach improves reliability and enhances the overall user experience, ensuring that devices stay relevant and functional over time.
Preparing for Your First OTA Rollout: A Step-by-Step Guide
OTA rollout requires careful planning, rigorous testing, and continuous monitoring to ensure that updates reach every device safely and efficiently. Success depends on thorough preparation, staged deployments, and active monitoring. Here is the ideal order of operations for prepping and rolling out a solid OTA infrastructure that will set your team up for success in the long term:
- Defining Your OTA Strategy
OTA must be designed from the start and not added as an afterthought. In this stage, teams establish a solid foundation by considering device architecture, security, storage, and compliance requirements. Key decisions include:
-
- Bootloader vs. Application OTA Logic: Teams must decide where the OTA update logic will reside. Application-based updates are often easier to implement and come with benefits like smaller payloads and fewer reboots. But they’re not a complete solution. While application-level OTA is useful for frequent updates, it doesn’t replace the need to update the full system image, including lower-level libraries and security components.
A bootloader-based OTA approach supports full-image updates and offers better recovery mechanisms, such as rollback support if an update fails. Ideally, teams should support both approaches. Relying on application-only OTA may seem faster at first, but it often leads to maintainability issues, missed security patches, and compliance gaps down the road. - Partitioning: Devices must have sufficient storage for dual-image updates or fallback mechanisms, ensuring that a failed update does not leave a device unusable.
- Proactive Release Monitoring: This involves monitoring the performance of releases as they roll out, using key health metrics such as stability and error rates. It gives teams early warning of regressions and enables fast, informed decisions before issues reach a larger portion of the fleet.
- Regulatory and Security Compliance: Meeting industry mandates, such as the Cyber Resilience Act, is critical for ensuring that OTA processes adhere to legal and security standards. Before an update is applied, cryptographic signing confirms that the firmware comes from a trusted source and has not been tampered with. This ensures that only the original device manufacturer can push updates, which is critical for preventing unauthorized modifications.Some teams also look to encrypt firmware updates to protect against reverse engineering. While possible, this approach is much harder to implement and requires early planning, including secure key storage and per-device encryption keys. For most teams, focusing on signing and authenticity checks provides strong protection without the added complexity.
- Bootloader vs. Application OTA Logic: Teams must decide where the OTA update logic will reside. Application-based updates are often easier to implement and come with benefits like smaller payloads and fewer reboots. But they’re not a complete solution. While application-level OTA is useful for frequent updates, it doesn’t replace the need to update the full system image, including lower-level libraries and security components.
The cloud-side setup ensures that updates are delivered securely and efficiently. Encrypted storage solutions, such as AWS S3 or Azure, safeguard update files from tampering. Device targeting logic, including cohort-based segmentation and phased deployments, helps control rollout risks.
- Pre-Deployment Testing and Validation
Before releasing OTA updates, teams conduct a series of tests to ensure the firmware performs as expected. Simulating updates in controlled environments helps identify issues before they impact real devices. Here are five critical tests teams should consider:
-
- Simulated OTA Updates: Runs OTA updates in a lab or staging environment before deployment, allowing teams to validate installation success and error handling in a controlled setting.
- Regression Testing: Confirms that new firmware is compatible with previous software versions, preventing unintended feature breaks or disruptions in functionality.
- Update Rollback Testing: Verifies that devices can seamlessly revert to a previous firmware version if an update fails or introduces new issues.
- Load and Scalability Testing: Evaluates how well the OTA infrastructure handles a large volume of simultaneous updates, ensuring stability under real-world conditions.
Check out this quick 15-second clip from three professional firmware engineers about how important OTA tests are:
We recommend achieving over 100 successful OTA test updates before a production release.
Just as important as the number of tests is how those updates are delivered. Use the same OTA system and process across development, QA, beta, and production environments. This ensures that any bugs or failures are caught early and in context, rather than appearing for the first time during a live rollout. Building confidence in the update path is key to scaling OTA safely.
- Initial Rollout to Internal Devices
The first stage of live deployment involves a controlled test group by deploying OTA updates to devices used by internal engineering teams. Automated monitoring tools track update success rates, error logs, and any failure points. A one to two weeks validation period is observed to confirm device stability before proceeding to a broader release.This is a key part of Memfault’s Proactive Release Monitoring methodology, which ensures that new firmware is healthy and stable before moving to wider cohorts. - Beta Release to Limited Fleet (Early Adopters and Testers)
During the beta phase, OTA updates are rolled out to a small percentage of the user fleet, typically between one and five percent. This cohort-based approach allows teams to monitor fleet health closely and identify any stability issues before scaling the update. In this stage, A/B testing and feature validation help compare the performance of new firmware against older versions. - Staged Rollout to Production Fleet
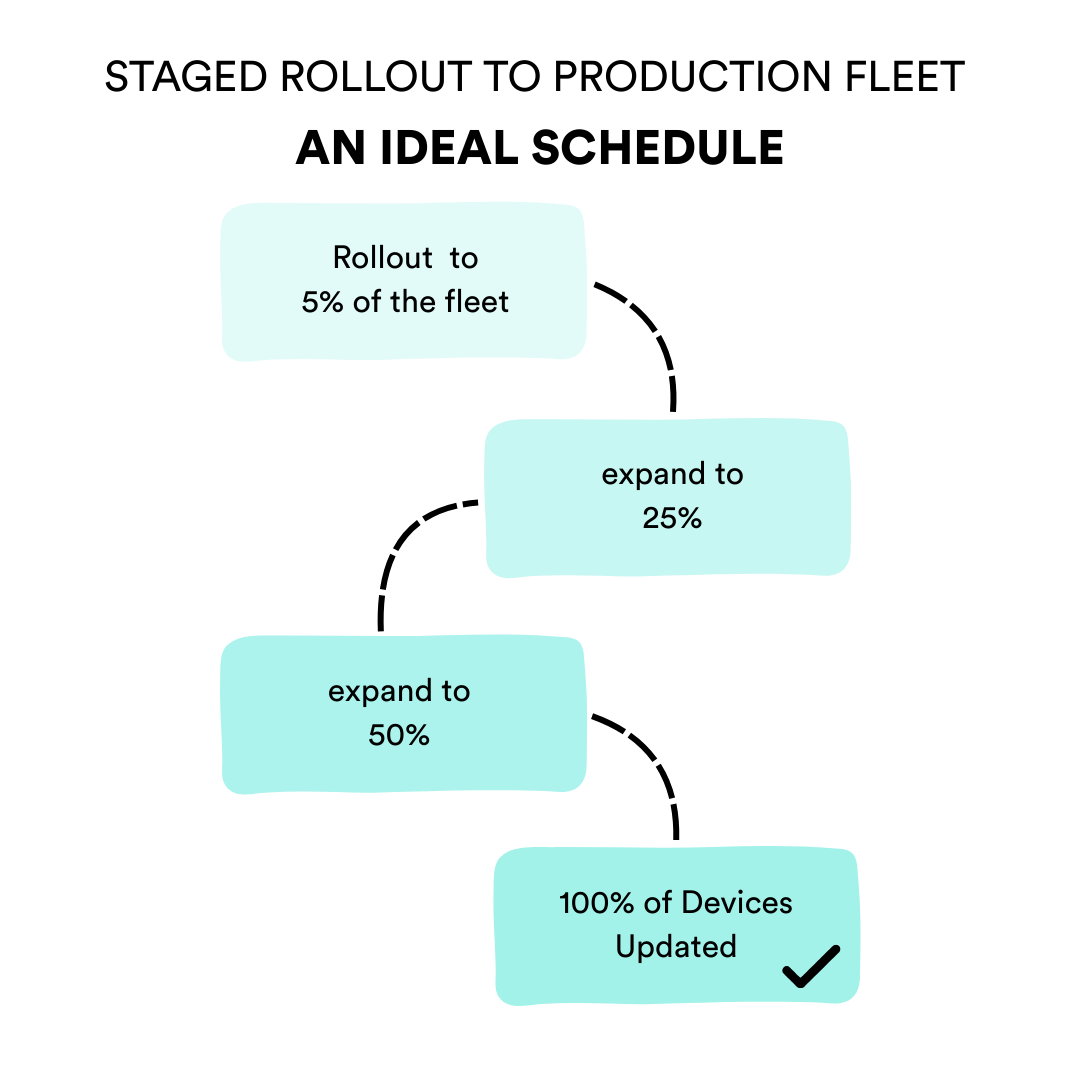
Next, the update is gradually scaled across the entire fleet, starting from a small percentage and increasing in stages. Here’s a typical tagged rollout schedule:
Week 1: If no major issues emerge in the beta phase, the rollout expands to 5% of the fleet.
Week 2: 25% of devices
Week 3: 50% of devices
Week 4: If all goes smoothly and all surfaced issues are troubleshooted, the update can reach the entire fleet. Final monitoring ensures performance remains stable across all devices.
Updates are scheduled during low-activity hours to prevent disruptions, and randomized check-ins are implemented to avoid overloading the cloud infrastructure. This prevents the Thundering Herd Effect, where too many devices request updates simultaneously, causing bandwidth congestion. Clear conditions should be defined to trigger a live rollback if any issues are detected.
- Post-Deployment Monitoring and Continuous Improvement
Once the update has been rolled out, continuous fleet monitoring is essential. Teams should track updated adoption rates, crashes, and any anomalies that arise during operation. Automated logging and debugging tools will be critical here to support root cause analysis for any failures.
The firmware optimization cycle is then refined based on device feedback and performance data, and an automated rollback plan is maintained for each new OTA update to ensure that every deployment has a fallback option in place.
Common Pitfalls for OTA IoT Deployment and How to Avoid Them
Even well-planned OTA deployments can run into issues if best practices aren’t followed. Here are the common pitfalls and how to mitigate them:
- Unstable updates can lead to bricked devices. Always validate updates through extensive pre-deployment testing and simulated OTA runs before release.
- Poor security practices expose IoT devices to hacking. Unauthenticated or unsigned firmware updates leave devices vulnerable to cyberattacks. Use cryptographic signing and secure boot mechanisms to install only trusted updates.
- No rollback plan increases the risk of deploying faulty firmware. Without a tested rollback mechanism, failed updates can leave fleets stranded. Implement automatic rollback capabilities to revert devices to a stable version when issues arise.
- Lack of observability creates blind spots in update success rates and errors. Without fleet-wide monitoring, it’s impossible to detect failures in real time. Integrate observability tools with OTA to track update adoption, performance, and failure logs.
- Most vendor OTA samples are not production-ready— don’t use them. Relying on generic semiconductor example code often leads to unoptimized or incomplete implementations. Customize and validate OTA processes to meet real-world production requirements.
- Hardcoded update URLs can cause fleet-wide failures. If a single update server goes offline, all devices may fail to receive updates. Use dynamic URL resolution and fallback mechanisms to prevent single points of failure.
Why OTA Updates Are a Smart Investment for IoT
Businesses that rely on manual updates face significant hidden costs, while those that invest in OTA gain a competitive edge.
The Hidden Costs of Manual Updates vs. OTA
Manual firmware updates drive up costs, causing downtime, lost revenue, and customer frustration. Unpatched devices expose companies to security breaches and compliance fines, while RMAs for software failures add unnecessary expenses. OTA eliminates these risks by enabling remote updates, reducing service costs, and keeping devices secure without manual intervention.
How OTA Saves Time & Money
OTA boosts efficiency by enabling instant security patches, reducing downtime, and ensuring compliance. It extends device lifespan through software optimizations and feature updates, keeping products relevant and improving customer satisfaction without costly recalls or replacements.
A well-executed OTA strategy helps companies move faster, reduce risk, and improve customer experience. As IoT fleets grow larger and more complex, OTA is no longer optional— it’s a strategic necessity for companies looking to scale efficiently while maintaining security and reliability.
Choosing the Right OTA IoT Solution
Choosing how to move forward with deploying OTA can be difficult. Here are a few key things to consider to make sure all goes smoothly:
- Device inventory to keep track of your fleet and the currently active software version on each device
- Managed release approval process to ensure every release gets the right level of approval before rolling out onto production devices
- Staged rollouts to control risk and test updates before full deployment
- Real-time monitoring to track update success rates and detect failures early
- Rollback mechanisms to revert devices instantly if something goes wrong
OTA is an infrastructure investment for the device’s lifetime. Choosing the right solution means ensuring every update is secure, efficient, and failsafe so that devices stay reliable without adding operational headaches.
Memfault: The Preferred OTA Solution for IoT Device Fleets
OTA updates shouldn’t feel like a gamble. Memfault provides end-to-end observability, giving teams complete visibility into update success rates, device health, and failure points, all in real time. Instead of pushing firmware blindly, engineers can track rollouts, detect issues early, and ensure every update improves device performance rather than introducing new risks.
Built for scale, Memfault is proven on millions of devices in the field and eliminates the friction of in-house OTA solutions with:
- Simple management of devices to update with cohorts
- Staged rollouts for automatically managed, controlled release rollouts
- Quick and easy Abort process with rollback mechanisms
- Built-in observability and monitoring so you never have to guess if your release is stable
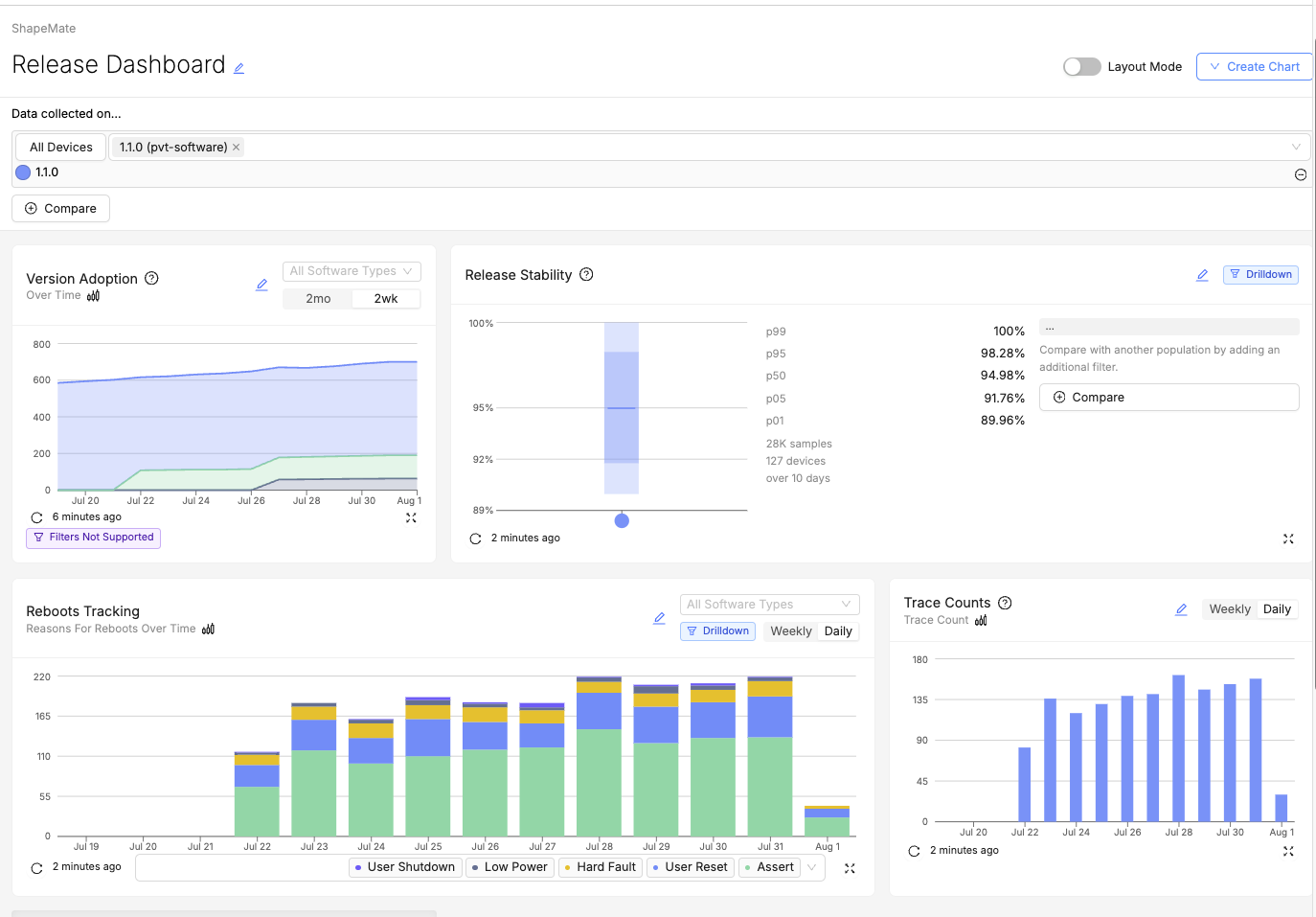
A screenshot of the OTA release dashboard in Memfault.
Embedded engineering teams who use Memfault avoid the hidden costs of maintaining custom infrastructure while gaining the control needed to ship updates confidently. Rollback support ensures devices return to a stable state if something goes wrong. Faster, safer, and smarter OTA— without the overhead.
Watch our expert-led webinar to discover best practices for building secure, scalable OTA update infrastructure, managing rollouts, and handling failures effectively.
Citations
- “The Economy of Things: The next value lever for telcos”, Raquel Katigbak, IBM.
- “Over-the-Air (OTA) Updates in Embedded Microcontroller Applications: Design Trade-Offs and Lessons Learned | Analog Devices”, Benjamin Bucklin Brown, Analog Devices.
- “Over-the-air Updates Using IoT: What Are They and How Do They Work?”, Emily Himes, PTC.
- “Over the Air (OTA) Update System – A Systematic Review”, Alochana Journal.
- “OTA – Deploying an Update to Production | Memfault Docs”, Memfault Blog.
- “EU Cyber Resilience Act: A Guide for Manufacturers & Developers”, Fraçois Baldassari, Memfault Blog.
- “Updating NVIDIA Jetson devices with Memfault OTA | Interrupt”, Thomas Sarlandie, Interrupt Blog | Memfault.
- “ISO/SAE 21434:2021 – Road vehicles — Cybersecurity engineering“, ISO.
FAQ
- What are the dangers of the OTA update process?
While OTA updates improve efficiency, they can introduce risks if not properly managed. Poorly tested updates can brick devices, security vulnerabilities in the update process can expose fleets to cyber threats, and a lack of rollback mechanisms can leave devices stranded with faulty firmware. Using a dedicated OTA platform with built-in observability, security, and rollback capabilities helps teams mitigate these risks and deploy updates with confidence. - How do staged OTA rollouts improve reliability?
Staged rollouts gradually deploy updates to small device groups before scaling to the entire fleet. This allows engineers to monitor performance, catch issues early, and prevent widespread failures. If problems arise, teams can halt the rollout, investigate, and apply fixes before resuming deployment. - What are the risks of not using OTA updates?
Without OTA updates, IoT devices risk running outdated firmware, exposing them to security threats, compliance violations, and performance degradation. Manual updates require costly on-site servicing and can lead to device recalls, increased RMAs, and dissatisfied customers. - When should OTA be implemented in the IoT development process?
OTA infrastructure should be planned from the beginning of the product development cycle, not as an afterthought. Decisions about bootloader design, security mechanisms, and storage capacity must be made early to ensure devices can support reliable and secure updates throughout their lifecycle. Waiting too long can result in costly redesigns and limited update capabilities. A purpose-built solution like Memfault simplifies early integration and ensures a scalable OTA strategy from day one. - What are the dangers of the OTA update process?
While OTA updates improve efficiency, they can introduce risks if not properly managed. Poorly tested updates can brick devices, security vulnerabilities in the update process can expose fleets to cyber threats, and a lack of rollback mechanisms can leave devices stranded with faulty firmware. Using a dedicated OTA platform with built-in observability, security, and rollback capabilities helps teams mitigate these risks and deploy updates with confidence.