Share
In 2025, OTA updates are a must-have for connected devices, but without robust testing, they can easily introduce critical failures. Over-the-air (OTA) updates make it possible to fix bugs, patch security holes, and roll out new features remotely. But one bad OTA update could introduce a performance regression, expose a new security vulnerability, or even brick devices in customer hands.
We explained what OTA is and how it works¹, but in this blog, we’ll dive into all things OTA testing.
Today, we’ll cover:
- What is OTA testing
- Common causes of OTA failure in production
- How to design for rollback, observability, and staged rollout
- Best practices for testing under real-world conditions
- How observability tools can help de-risk OTA updates at scale
TL;DR
- OTA (Over-the-Air) updates² allow embedded teams to remotely deploy updated software to devices in the field. They can be used to fix bugs, patch vulnerabilities, and deploy new features remotely, but if not tested rigorously can also introduce new software issues, damaging brand reputation and customer trust.
- To avoid failures during updates, teams must test OTA firmware under real-world conditions, implement robust rollback mechanisms, and adopt staged rollouts backed by reliable observability tools.
- This guide walks through practical strategies from dual-bank architecture to failure simulation and secure signing that can help ship OTA updates with confidence.
- We’ll also cover how observability tools can help de-risk OTA with real-time fleet monitoring, staged rollouts, cohort-based deployments, and post-update stability metrics.
Learn hard-won lessons from engineering leaders who’ve built and maintained OTA systems at scale.
Watch the full live session→: The secrets to building secure & scalable OTA infrastructure with Nick Sinas
What is OTA testing?
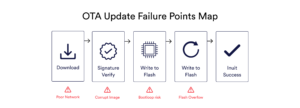
OTA (Over-the-Air) testing³ is the process of validating that firmware updates can be remotely delivered, installed, and executed on embedded or IoT devices without causing system failure. Pre-launch testing ensures that the update package can be securely downloaded, its integrity verified, written to the correct memory location, and successfully booted into production.
Proper OTA testing confirms that devices behave as expected after the update and can robustly handle conditions like poor connectivity, low power, or intermittent restarts. This safeguards against a worst-case scenario where corrupted firmware is installed on a device in the field.
Why is OTA testing before launch important?
OTA testing before production rollout is crucial because it’s the final gate before firmware hits production devices with no undo button. Firmware is a critical layer of any connected product, and once deployed, updates are often the only way to fix bugs, patch security vulnerabilities⁴, or improve performance.
If OTA functionality isn’t thoroughly tested before release, a failed update can have serious downstream consequences⁵, including:
- High RMA and field servicing costs
- Lost customer trust and product reputation
- Missed compliance obligations (especially in regulated or safety-critical environments)
- Delays in feature rollouts and security patches
The OTA Testing Process
Effective OTA testing ensures that firmware updates can be delivered safely, reliably, and securely across distributed IoT device fleets. A thorough OTA testing process should include:
- Firmware image validation: Verify that the OTA update package is signed, hashed, and sized correctly for the intended hardware and software version constraints.
- Recovery and rollback testing: Ensure devices have a mechanism to recover in the event of a bad or corrupted update.
- Failure scenario simulation: Intentionally introduce issues like incomplete downloads, corrupt firmware files, or power loss during install to validate system resilience.
- Field network condition testing: Assess OTA performance in unstable environments, including weak signal strength, intermittent connectivity, and long install durations.
- Post-update device monitoring: Track boot success, memory usage, error rates, and telemetry data after updates to catch regressions or instability early.
- Secure boot and authentication checks: Confirm that updated firmware is properly authenticated and that the device enforces secure boot policies at runtime.
It’s important to note that OTA testing requires robust processes and reliable tools. Before we discuss the mitigation strategies, let’s examine the most common failure points in OTA firmware delivery and deployment.
The most common ways OTA can go wrong
OTA failures happen. Many embedded teams have experienced the consequences firsthand, from interrupted updates that brick devices to broken logic that entirely prevents future updates.
Here are the most common ways OTA can go wrong:
1. Bricking due to partial or interrupted updates
Power loss or network failure during a write operation can leave the device in an inconsistent state. If there’s no fallback mechanism or second firmware slot, the device may not boot at all.
2. OTA logic that breaks future updates
This is a particularly insidious issue in which the update appears successful but breaks the OTA mechanism itself. The next update can’t be received, trapping the device on a faulty version. This has happened in startups and at scale. Companies like Apple have dealt with variations of this.
This is particularly relevant for Linux-based embedded systems, and many engineers are already finding creative ways to handle OTA updates on Embedded Linux in the wild.
Check out this story from Memfault Co-founder and CTO, Chris Coleman, about a time when he and his team accidentally broke the future OTA with an OTA update.
3. Security flaws in firmware validation
Proper OTA security depends on verifying that each firmware update is authentic before it’s installed. Missing or improperly enforced signature checks, or the use of hardcoded public keys can expose devices to unauthorized code execution or cause valid updates to fail.
4. Thundering Herd problem
When thousands of devices request updates simultaneously, poorly designed backend systems collapse. This problem is also referred to as the thundering herd problem⁶. A single update server point of failure or inadequate capacity could lead to partial downloads and corrupted updates. Implement staggered rollouts, CDN distribution, and load testing before deploying to your entire fleet.
5. Update size exceeds available flash memory
Firmware grows larger over time as features expand. Updates that exceed available flash space silently fail or corrupt adjacent memory regions. This happens frequently when initial partition sizing doesn’t account for future growth. Always verify that your update will fit in the target partition before deployment, especially with A/B update schemes that require double the storage.
6. Hardware variant incompatibility causes failures
Product evolution creates hardware fragmentation as components change. Firmware built for specific revisions often requires particular hardware configurations. Sending the wrong firmware to incompatible hardware disables peripherals or triggers unpredictable behavior. Implement robust device identification to ensure only compatible firmware reaches specific hardware variants.
7. Vendor reference code fails in real-world conditions
Most engineering teams start with OTA examples from chip vendors. These demonstrate basic functionality but lack production-grade reliability. Error handling, recovery logic, and verification steps are typically simplified in these samples. Don’t deploy vendor code without thorough hardening for real-world conditions, including network instability and power fluctuations.
8. Battery drain from power management bugs
Updates can introduce subtle power management flaws that only become apparent when batteries drain unexpectedly fast. Firmware bugs prevent devices from entering sleep states or trigger continuous background processes. Measure power consumption before and after updates to catch these silent battery killers before deployment.
Five proven strategies to test OTA firmware updates without bricking devices
Testing OTA updates is essential to prevent bricked devices, broken rollout logic, or update failures in the field. We’ve collated battle-tested strategies that can help firmware teams build confidence in the OTA update process, minimize risk across a fleet, and ensure that even the worst-case update scenario doesn’t result in bricked devices.
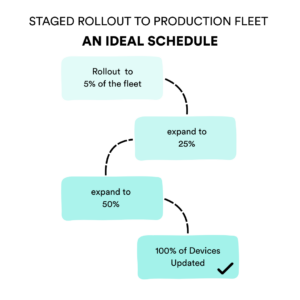
1. Use staged rollouts and cohorts
Never deploy to your entire device fleet at once. Instead, use cohort-based rollouts to release firmware updates incrementally:
- Start with internal test devices in controlled environments
- Expand to a beta cohort, which users can opt into to run pre-release updates on their device
- Roll out in phases (5%, 25%, 50%, 100%), monitoring each wave
Each cohort acts as a risk buffer. If something breaks early, you can pause the rollout, fix the issue, and avoid fleet-wide failure. OTA platforms like Memfault make it easy to segment your fleet and track rollout performance by version, geography, hardware SKU, or user group.
This is your first line of defense. A staged rollout with observability is often the only way to prevent a 1% failure from becoming a 100% catastrophe.
2. Implement dual-bank architecture and automated rollback
A dual-bank (or A/B) update system maintains two firmware slots: the active image and a backup. The new firmware is downloaded to the inactive slot. After validation, the bootloader switches to boot from the new image.
If the device fails to boot or run correctly:
- A watchdog timer or health check triggers a rollback
- The bootloader reverts to the previous known-good firmware
- The device recovers autonomously without human intervention
Memfault’s OTA documentation⁷ outlines dual-bank and bootloader integration strategies if you’re designing a rollback-aware system.
3. Simulate real-world conditions
OTA in the lab is one thing, and OTA in the field is another. You should assume that devices in the field are being placed in less-than-ideal environments. You should plan for devices to update over unstable Wi-Fi, cellular, or mesh connections; sometimes while on battery, moving between networks, or in noisy RF environments.
Your OTA testing should simulate:
- Poor signal strength and dropped packets
- Slow bandwidth and high-latency downloads
- Power loss during download, validation, or flashing
- Mid-update reboots or disconnects
4. Test failure modes intentionally
A robust OTA system should behave predictably under failure and recover automatically when possible. Test these scenarios deliberately:
- Apply a corrupted or unsigned firmware image
- Simulate file system corruption or flash write failure
- Use malformed metadata (e.g., invalid versioning or checksum)
- Force boot failure (e.g., by modifying a critical init routine)
5. Monitor OTA updates with observability and metrics
Deployment is the beginning of validation. Use OTA observability tools to:
- Track update success/failure rates across cohorts
- Monitor post-update health (e.g., crash rate, reboot loops, error logs)
- Establish rollout criteria based on device-hours of coverage and stability thresholds
- Alert when metrics drop below defined thresholds (e.g., <99.9% stability)
To ensure reliability at scale, we recommend running at least 100 successful OTA test updates across representative hardware variants before promoting any firmware to production. This helps surface regression bugs, memory issues, or compatibility gaps that may not show up in lab tests alone.
OTA testing checklist for engineering teams
Before pushing firmware updates over the air, engineering teams must ensure that updates will apply successfully under all expected (and unexpected) conditions. Devices operating on limited connectivity, strict memory budgets, or safety-critical use cases can’t afford to brick during deployment.
Before you deploy, ask:
- Can the update recover from failure?
If something goes wrong mid-install, will the device automatically roll back to a safe state? - Can you detect issues immediately after rollout?
Are you tracking update success, system stability, and error rates across cohorts? - Can you stop or pause rollouts in production?
Do you have control to halt updates, isolate problems, and prevent wider impact?
If the answer to any of these is uncertain, now is the time to improve your OTA testing strategy before your next release.
Scale OTA testing with confidence using Memfault
Deploy firmware updates without guessing what will happen next. Memfault gives firmware and embedded teams full visibility and control over OTA updates, so you can ship faster, catch issues earlier, and recover quickly when things go wrong.
Target updates by cohort, monitor real-time stability, and pause rollouts the moment metrics deviate from the expected baseline. With automatic diagnostic data from affected devices, you can debug without physical access or manual log collection.
Built to integrate with your existing firmware stack, regardless of OS, connectivity path, or hardware. Memfault brings modern OTA workflows to any embedded system.
Want to learn how leading engineering teams approach secure, scalable OTA infrastructure?
Watch the Coredump Session episode where we dive into the secrets to building secure and scalable OTA update infrastructure
Citations
- “OTA IoT Breakdown: What OTA Is and How It Works in IoT”, Siara Singleton, Memfault.
- “Over-the-air Updates Using IoT: What Are They and How Do They Work? | PTC”, Emily Himes, PTC.
- “The Secrets to Building Secure & Scalable OTA Update Infrastructure”, Memfault.
- “Over the air updates (OTA): best practices for device safety”, Caitlin Gittins, IoT Insider.
- “5 Common OTA Update Mistakes to Avoid”, Martin Donadieu, Capgo.
- “Thundering herd problem”, Wikipedia.
- “Over-the-Air Updates (OTA) | Memfault Docs” Memfault Docs.
FAQ
- What is OTA testing in embedded systems?
OTA testing ensures your firmware updates can be safely delivered to devices in the field without requiring physical access. Unlike traditional software testing, embedded OTA testing must account for limited resources, unexpected power cycles, and recovery mechanisms that prevent bricking. Think of it as verifying your update system’s resilience against real-world conditions that embedded devices face daily. - How do you test OTA firmware updates for IoT devices?
Testing OTA updates for IoT devices requires simulating real-world deployment conditions beyond ideal lab environments. Effective testing includes verifying behavior during connectivity interruptions, unexpected power cycles, partial downloads, and installation failures. - What causes OTA updates to fail?
OTA update failures stem from multiple technical factors that impact deployment reliability. Common causes include unexpected power interruptions during critical write operations, corrupted firmware downloads due to network instability, failed cryptographic verification of signed images, insufficient storage space for temporary files, and inadequate recovery logic, such as missing rollback support. - How can I prevent bricked devices during OTA updates?
Preventing bricked devices during updates requires implementing multiple defensive measures in your firmware architecture. Key strategies include A/B partitioning for failsafe updates, staged rollouts to contain potential damage, cryptographic signature verification to prevent corrupted installs, pre-update validation tests, robust error handling, and post-update monitoring systems. - What is a staged OTA rollout?
A staged OTA rollout is a strategic deployment technique where firmware updates are released incrementally to defined device cohorts rather than simultaneously to the entire fleet. This methodical approach allows engineering teams to monitor initial performance on a limited subset of devices, identify potential regressions or compatibility issues early, and prevent widespread failures. - How do I monitor OTA update success?
Monitoring OTA success requires tracking multiple technical indicators throughout the deployment lifecycle. Effective monitoring includes measuring firmware adoption rates across device cohorts, analyzing crash-free runtime after updates, monitoring memory usage trends, identifying error rate spikes, tracking rollback events, and collecting performance metrics that validate stability. - Why is rollback support important in OTA testing?
Rollback support provides a critical safety mechanism that enables devices to restore previous firmware when updates introduce stability issues or functional regressions. This capability preserves device operability even when unexpected problems bypass testing protocols. - What is the best way to test OTA on embedded Linux or MCU devices?
Testing OTA on embedded Linux and MCU devices requires platform-specific approaches that address their unique constraints. Best practices include simulating power and connectivity failures during critical update stages, validating cryptographic signature verification for security, testing bootloader behavior under various failure conditions, and verifying resource efficiency. For resource-constrained MCUs, additional focus on memory usage, flash wear leveling, and optimizing update packages significantly improves reliability.